Introduction to Bluetooth Technology and Its Popularity
Bluetooth technology is a wireless communication protocol that enables devices to connect and share data over short distances. It was first developed in the 1990s by Ericsson, but has since become widely adopted by various industries and individuals around the world.
One of the main reasons for Bluetooth’s popularity is its versatility. It can be used for a wide range of applications, such as connecting wireless headphones to a smartphone, transferring files between devices, and controlling smart home devices.
Bluetooth technology has also evolved over time, with newer versions offering faster data transfer speeds and longer range. Bluetooth Low Energy (BLE), for example, is a newer version of the technology that is specifically designed for low-power devices and Internet of Things (IoT) applications.
Overall, Bluetooth technology has become an integral part of modern society, enabling convenient and efficient communication and data sharing between devices.
Understanding the Bluetooth Security Risks
Bluetooth technology has become a common feature of modern devices, from smartphones and laptops to smart home devices and cars. While Bluetooth offers convenient wireless connectivity, it also poses potential security risks that users should be aware of.
One major risk is the possibility of unauthorized access or interception of data transmitted over Bluetooth connections. Attackers can use various techniques, such as Bluetooth scanning and spoofing, to gain access to sensitive data or take control of connected devices.
Another risk is the potential for Bluetooth-enabled devices to be hacked or infected with malware. Attackers can exploit vulnerabilities in the Bluetooth software or use social engineering tactics to trick users into downloading malicious files or apps.
To reduce the risks associated with Bluetooth technology, it’s important to keep devices up-to-date with the latest security patches and to use strong passwords for Bluetooth connections. Users should also be cautious when pairing devices with unfamiliar or untrusted sources, and avoid using Bluetooth in public places where it could be easily intercepted.
How Hackers Exploit Bluetooth Vulnerabilities
Bluetooth vulnerabilities can be exploited by hackers to gain unauthorized access to devices or steal sensitive data. One common technique used by hackers is “bluejacking,” which involves sending unsolicited messages or files to nearby Bluetooth devices. This can be used to distribute malware or phishing attacks.
Another technique is “bluebugging,” which involves taking control of a Bluetooth device and using it to make calls, send messages, or access data. This is often done by exploiting vulnerabilities in the Bluetooth software or using brute-force attacks to guess the device’s PIN.
“Bluesnarfing” is another technique used by hackers to steal data from Bluetooth-enabled devices, such as contacts, messages, and photos. This is done by exploiting vulnerabilities in the Bluetooth protocol and accessing the device’s file system.
To protect against Bluetooth vulnerabilities, users should keep their devices updated with the latest security patches and avoid pairing with unfamiliar or untrusted sources. It’s also important to use strong passwords for Bluetooth connections and to be cautious of unsolicited messages or files.
The Risks of Using Bluetooth in Public Places
Using Bluetooth in public places can pose several risks to users. One major risk is the potential for eavesdropping, where attackers can intercept Bluetooth signals and access sensitive data transmitted between devices. This can include login credentials, financial information, or personal messages.
Another risk is the potential for device pairing with unknown or malicious sources. Attackers can use techniques like “bluejacking” or “bluesnarfing” to gain access to devices or steal data. This is especially dangerous in public places, where attackers may be able to blend in with the crowd and go unnoticed.
To reduce the risks of using Bluetooth in public places, users should ensure that their devices are not discoverable when not in use, and should only pair with trusted sources. Users should also avoid transmitting sensitive data over Bluetooth in public places and consider using a virtual private network (VPN) to encrypt their connections. Finally, keeping Bluetooth devices up-to-date with the latest security patches is also important for minimizing the risk of attacks.
The Risks of Pairing Your Device with Unknown Bluetooth Devices
Pairing your device with an unknown Bluetooth device can pose several risks to your security and privacy. Unknown devices may be owned by attackers who can use various techniques to exploit vulnerabilities in your device and steal your sensitive information or take control of your device.
Attackers can also use pairing as a social engineering tactic to trick users into accepting a malicious connection, leading to unauthorized access to the device and its data. This can be especially dangerous when the device contains sensitive information or has access to critical systems.
To mitigate the risks of pairing your device with unknown Bluetooth devices, it’s important to ensure that Bluetooth is turned off when not in use and only connect to devices that are trusted and known to be secure. It’s also important to keep devices updated with the latest security patches to reduce the risk of vulnerabilities being exploited. Finally, being vigilant of suspicious pairing requests and not accepting them can help prevent unauthorized access.
Tips for Securing Your Bluetooth Devices and Connections
Bluetooth technology is commonly used for wireless communication between devices, but it can also pose a security risk if not secured properly. Here are some tips for securing your Bluetooth devices and connections:
- Keep your devices updated: Regularly update your Bluetooth devices with the latest software updates and security patches to fix any known vulnerabilities.
- Use a strong password: Set a strong and unique password for your Bluetooth devices and connections to prevent unauthorized access.
- Turn off Bluetooth when not in use: This can prevent attackers from exploiting vulnerabilities in your Bluetooth devices.
- Avoid using public Bluetooth connections: Public Wi-Fi and Bluetooth connections can be compromised by attackers, so it’s best to avoid using them.
- Only pair with trusted devices: Only pair your devices with known and trusted devices to prevent unauthorized access.
By following these tips, you can help to secure your Bluetooth devices and connections and reduce the risk of security breaches and data theft.
How to Disable or Turn Off Bluetooth When Not in Use
Disabling or turning off Bluetooth when not in use is an effective way to prevent security breaches and protect your personal data. Here’s how to do it:
On Windows:
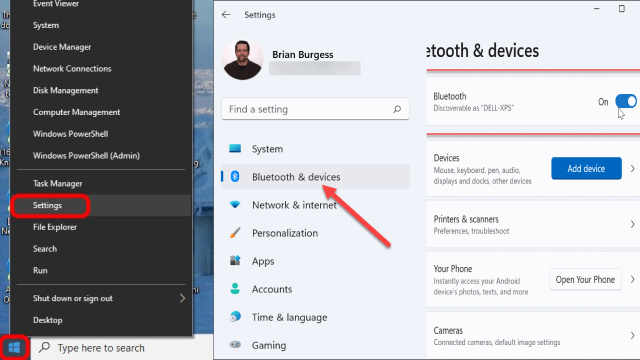
- Click the Start button and go to Settings.
- Select Devices and click on Bluetooth & other devices.
- Toggle the Bluetooth switch to Off.
On Mac:
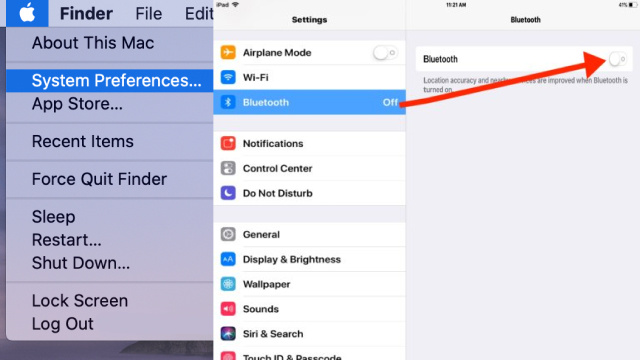
- Click on the Apple menu and select System Preferences.
- Click on Bluetooth and toggle the Bluetooth switch to Off.
On Android:
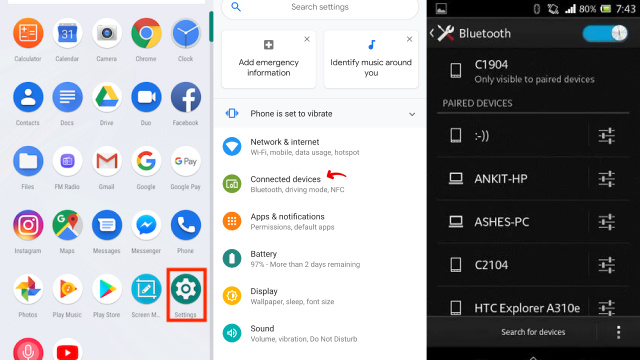
- Open the Settings app.
- Tap on Connected devices.
- Tap on the Bluetooth toggle to turn it off.
On iOS:
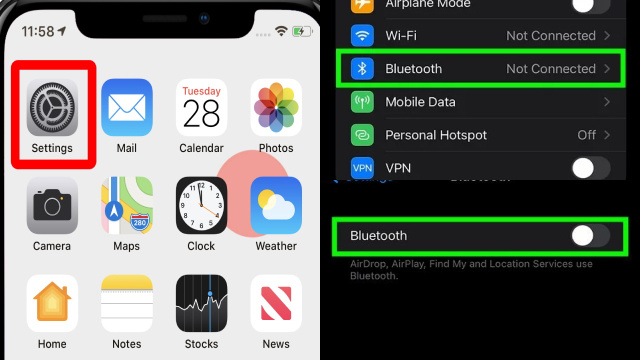
- Go to Settings.
- Tap on Bluetooth.
- Toggle the Bluetooth switch to Off.
By turning off Bluetooth when not in use, you can prevent unauthorized access to your device and reduce the risk of security breaches. It’s a simple and effective way to protect your personal data.
Emerging Technologies to Enhance Bluetooth Security
The modern digital ecosystem relies increasingly on Bluetooth technology, making the security of this technology critically important. As Bluetooth devices become ubiquitous in our lives, from smartphones and laptops to smart home appliances, it’s essential to enhance Bluetooth security to protect personal and sensitive data.
Fortunately, emerging technologies offer promising solutions to bolster Bluetooth security. One such technology is Bluetooth 5.0 and its successors, which have improved encryption and security features. These advancements make it more challenging for attackers to intercept Bluetooth communications.
Additionally, the implementation of biometric authentication, such as fingerprint or facial recognition, in Bluetooth devices adds an extra layer of security. This ensures that only authorized users can access the devices and their data.
Moreover, the integration of blockchain technology can enhance Bluetooth security by creating a tamper-proof record of device interactions. This makes it virtually impossible for malicious actors to manipulate the data exchanged between Bluetooth devices.
Machine learning and artificial intelligence are also being utilized to identify and mitigate Bluetooth vulnerabilities in real-time. They can detect unusual patterns of behavior, helping to thwart potential attacks.
In conclusion, emerging technologies hold great promise for enhancing Bluetooth security. With Bluetooth’s continued integration into our daily lives, these advancements are crucial in safeguarding our digital privacy and personal information.
The Future of Bluetooth Security and What to Expect
As Bluetooth technology becomes more widespread and integrated into everyday devices, the importance of securing these connections will only grow. The future of Bluetooth security will likely see advancements in encryption methods, with stronger and more complex algorithms used to protect data being transmitted over Bluetooth connections. Additionally, device manufacturers may develop new security features, such as automatic device pairing and biometric authentication, to ensure that only authorized users can access Bluetooth connections.
However, as with any technological advancement, there will always be new vulnerabilities and potential security risks to be addressed. As such, it will be important for both manufacturers and users to remain vigilant and stay up-to-date on the latest security measures and best practices for using Bluetooth technology safely and securely. By doing so, we can ensure that Bluetooth remains a reliable and secure means of communication for years to come.