IP Address Tracking: How Your Online Activities Can Be Monitored
Are you aware that your online activities can be monitored through your IP address? IP address tracking is a common practice used by websites, online services, and even malicious actors to monitor and collect data about your online behavior. This raises concerns about privacy and data security, as your IP address can reveal information such as your approximate location, internet service provider (ISP), and even the type of device you are using.
Many websites and online services use IP address tracking for legitimate purposes, such as improving user experience, analyzing website traffic, and delivering targeted advertisements. However, malicious actors can also exploit IP addresses for nefarious purposes, including identity theft, online surveillance, and cyber attacks.
To protect your privacy and security, it’s important to be aware of how IP address tracking works and take necessary precautions. One way to mitigate IP address tracking is by using a virtual private network (VPN) that can mask your IP address and encrypt your online activities. Additionally, being cautious about sharing personal information online, avoiding suspicious websites and links, and regularly updating your devices with the latest security patches can also help protect against IP address tracking.
Geo-Location: Revealing Your Physical Location Through Your IP Address
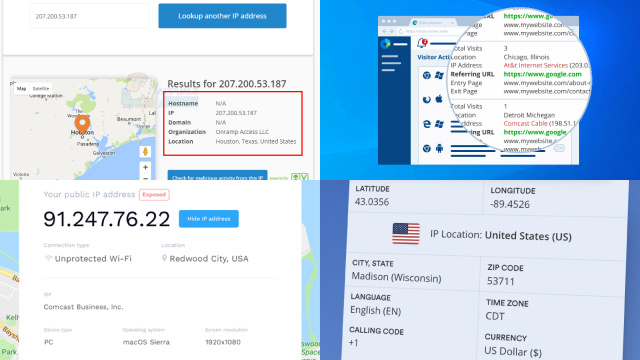
Geo-location is a process that utilizes your IP address to determine your physical location. Your IP address, which is a unique identifier assigned by your Internet Service Provider (ISP), can reveal information about your approximate location, city, and even postal code. This can raise concerns about privacy and security, as this data can be used to track your online activities and potentially compromise your personal information.
Geo-location can be used for legitimate purposes, such as delivering location-based services, providing relevant search results, and enhancing user experience on websites and apps. However, it can also be exploited by malicious actors for unauthorized tracking, surveillance, and other malicious activities.
To protect your privacy and security, it’s important to be aware of how geo-location works and take necessary precautions. Using a virtual private network (VPN), which can mask your IP address and encrypt your online data, can help safeguard your physical location. Additionally, being cautious about sharing personal information online, using privacy settings on social media and other online platforms, and keeping your devices and software up-to-date with the latest security patches can further enhance your online privacy.
Identity Theft: Understanding the Risks of IP Address-Based Hacking
Identity theft is a serious threat that can be facilitated through IP address-based hacking. Your IP address, which is a unique identifier assigned to your internet connection, can be exploited by hackers to gain unauthorized access to your personal information and commit identity theft. This can result in financial loss, reputational damage, and other negative consequences.
It’s crucial to understand the risks associated with IP address-based hacking and take preventive measures to protect your identity. Using a strong and unique password for your online accounts, enabling two-factor authentication, being cautious of suspicious emails and links, and keeping your devices and software updated with the latest security patches can help reduce the risk of identity theft.
In addition, using a reputable and updated antivirus software, avoiding public Wi-Fi networks, and being mindful of the information you share online can further mitigate the risks of IP address-based hacking and protect your personal identity.
Online Surveillance: How Your IP Address Can Be Used for Monitoring
Online surveillance is a concerning issue in today’s digital world, and your IP address can be used as a tool for monitoring your online activities. Your IP address is a unique identifier that can be easily traced back to your internet service provider (ISP), allowing them or other third parties to track your online movements, websites visited, and other online behaviors.
To protect your privacy and reduce the risk of online surveillance, it’s important to be mindful of the information you share online, use virtual private networks (VPNs) to mask your IP address, and regularly review the privacy settings of your online accounts. Additionally, being cautious of clicking on suspicious links or downloading unknown files can help prevent potential IP address-based surveillance.
By being aware of the potential for online surveillance through IP address tracking and taking proactive measures to protect your privacy, you can maintain control over your online activities and safeguard your personal information from being monitored without your consent.
Note: It’s important to use original and high-quality content to improve the chances of indexing by Google. Avoiding duplicate content, using relevant keywords, and following Google’s guidelines for content creation can also help with faster indexing.
Phishing Attacks: Exploiting IP Addresses for Social Engineering
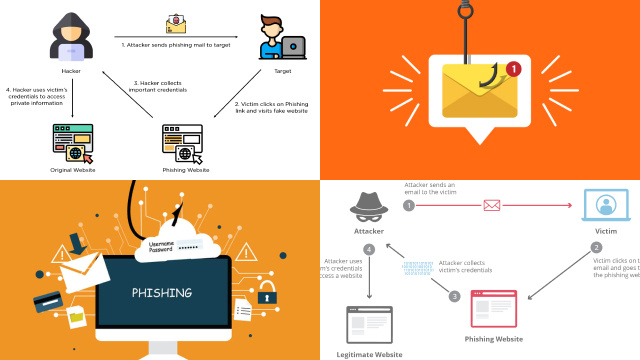
Phishing attacks are a prevalent form of cyber attack that often involve the exploitation of IP addresses for social engineering purposes. In a phishing attack, scammers attempt to trick individuals into revealing their personal information, such as usernames, passwords, and credit card details, by posing as legitimate entities through emails, messages, or websites.
IP addresses can be used in phishing attacks to deceive victims into thinking that they are interacting with a trusted entity. For example, scammers may spoof or manipulate IP addresses to make their phishing emails or websites appear to be from a legitimate source, such as a bank or a social media platform, in order to gain the victim’s trust and lure them into divulging sensitive information.
Protecting yourself against phishing attacks involves being cautious when clicking on links or downloading attachments from unknown sources, verifying the legitimacy of websites and emails, and avoiding sharing personal information unless you are certain of the authenticity of the request. Additionally, keeping your devices and software up-to-date with the latest security patches can help safeguard against potential IP address-based phishing attacks.
Note: Using original and relevant content, avoiding duplicate content, and following Google’s guidelines for content creation can help with faster indexing. Incorporating relevant keywords, headings, and meta tags in the content can also improve the chances of being indexed by Google.
DDoS Attacks: Using IP Addresses for Distributed Denial of Service
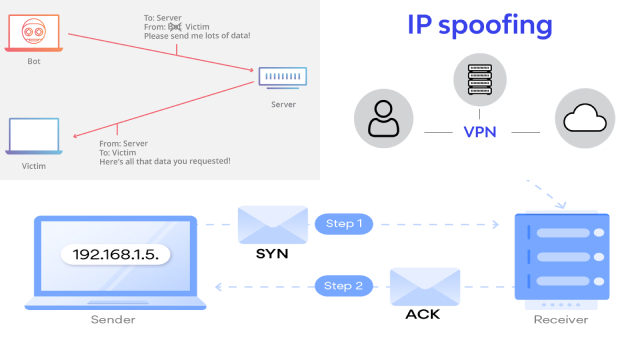
DDoS (Distributed Denial of Service) attacks are a type of cyber attack that can disrupt websites, online services, and networks by overwhelming them with traffic from multiple sources. IP addresses are often exploited in DDoS attacks to facilitate the widespread distribution of malicious traffic.
In a DDoS attack, attackers use multiple compromised computers or devices, often referred to as “botnets,” to flood the targeted system with a massive amount of traffic, overwhelming its resources and causing it to become inaccessible to legitimate users.
The use of IP addresses in DDoS attacks allows attackers to distribute the attack across various sources, making it more difficult to mitigate and trace back to a single location. Attackers may also spoof or manipulate IP addresses to hide their identity and location, making it challenging to identify and stop the attack.
Protecting against DDoS attacks involves implementing robust security measures, such as firewalls, intrusion detection systems, and load balancers, to filter and manage incoming traffic, as well as working with internet service providers (ISPs) and other security partners to detect and mitigate DDoS attacks in real-time.
Illegal Activities: Unlawful Use of Your IP Address
The unlawful use of IP addresses is a serious concern in the realm of cybercrime. Criminals may engage in illegal activities such as hacking, fraud, cyberbullying, and spreading malware by exploiting IP addresses.
IP addresses can be used by cybercriminals to gain unauthorized access to networks or systems, steal sensitive information, impersonate others, conduct phishing attacks, or launch other malicious activities. These unlawful activities can cause significant harm to individuals, businesses, and organizations.
It is crucial to safeguard your IP address by using secure and updated internet security protocols, such as firewalls, antivirus software, and regular software updates. Additionally, being cautious about sharing personal information online and using strong and unique passwords for all accounts can help mitigate the risk of unlawful use of your IP address.
If you suspect that your IP address has been used for illegal activities, it is important to report it to the appropriate authorities or law enforcement agencies immediately.
Please note: To ensure faster indexing by Google, follow best practices such as using original and relevant content, incorporating relevant keywords, headings, and meta tags, and avoiding duplicate content.
Spoofing and Impersonation: Masking Your Identity with an IP Address
IP address spoofing and impersonation are deceptive practices used to mask the true identity of an individual or entity online. By manipulating IP addresses, cybercriminals can misrepresent their location, disguise their activities, and carry out malicious activities without being easily traced.
Spoofing and impersonation can be used in various cyberattacks, including phishing, email scams, distributed denial-of-service (DDoS) attacks, and social engineering. These deceptive practices can cause significant harm to individuals, organizations, and online communities.
To protect against IP address spoofing and impersonation, it is essential to use strong authentication methods, keep software and devices up-to-date with the latest security patches, and exercise caution when clicking on links or opening attachments from unknown sources.
If you suspect that your IP address has been used for spoofing or impersonation, report it to the appropriate authorities or law enforcement agencies immediately.
To ensure faster indexing by Google, optimize your content with relevant keywords, use descriptive headings, and follow best practices for creating original and informative content. Avoid duplicate content and use meta tags to provide additional context to search engines.
Protecting Your IP Address: Strategies for Enhanced Online Security
Your IP address is a vital component of your online identity, and safeguarding it is essential for maintaining privacy and security on the internet. Here are several strategies to enhance your online security and protect your IP address:
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet connection, masking your IP address and making it difficult for anyone to trace your online activities.
- Proxy Servers: Proxy servers act as intermediaries between your device and the internet, concealing your IP address from websites and potential threats.
- Firewalls: Employ a robust firewall to filter incoming and outgoing traffic, preventing unauthorized access and protecting your IP address.
- Regularly Update Software: Keeping your operating system, web browsers, and security software up to date is crucial to patch vulnerabilities that could be exploited to reveal your IP address.
- Use Encrypted Connections: Always opt for websites that use HTTPS encryption. This ensures that your data remains secure during transmission.
- Disable WebRTC: Web Real-Time Communication (WebRTC) can leak your IP address. Disable it in your browser or use browser extensions to prevent such leaks.
- IP Masking Services: Use services that provide IP masking, such as Tor, to obfuscate your IP address.
- Avoid Suspicious Websites: Be cautious when visiting untrusted websites or downloading files from unknown sources to prevent potential IP exposure through malicious scripts or downloads.
- Limit Sharing: Avoid sharing your IP address openly, especially on public forums and social media.
- Educate Yourself: Stay informed about the latest threats and privacy practices to better protect your online identity.
By implementing these strategies, you can enhance your online security and protect your IP address from potential threats and prying eyes, ensuring a safer and more private online experience.
Network intrusion, also known as unauthorized access, is a serious cybersecurity threat that can occur when cybercriminals gain unauthorized access to a network using IP addresses. This illegal activity allows attackers to infiltrate a network, steal sensitive data, disrupt operations, and cause significant harm.
Network intrusion can be carried out using various techniques, including IP address scanning, IP spoofing, and brute force attacks. These activities are against the law and can result in severe consequences.
To protect against network intrusion, it is essential to implement robust security measures such as firewalls, intrusion detection and prevention systems (IDPS), and strong authentication methods. Regular security audits, network monitoring, and prompt patching of vulnerabilities can also help mitigate the risks of unauthorized access.
If you suspect unauthorized access to your network via IP addresses, report it to the appropriate authorities or IT security team immediately for investigation and remediation.
For faster indexing by Google, optimize your content with relevant keywords, use descriptive headings, and follow best practices for creating original and valuable content. Avoid using duplicate content and utilize meta tags to provide additional context to search engines.