Introduction to Phone Hacking
Phone hacking is the act of gaining unauthorized access to a mobile device, typically for the purpose of obtaining personal or sensitive information. This can include accessing emails, text messages, phone logs, and other data stored on the device.
Phone hacking can be carried out through various methods, including exploiting software vulnerabilities, social engineering techniques, and physical access to the device.
The consequences of phone hacking can be severe, including identity theft, financial fraud, and reputational damage. Additionally, phone hacking can be a violation of privacy and can result in legal consequences for the hacker.
To prevent phone hacking, it is important to use strong passwords, keep your device’s software up to date, and be cautious when opening email attachments or clicking on links from unknown sources. Additionally, you should be aware of the signs of a hacked device, such as unusual behavior or activity on the device, and take action if you suspect that your device has been compromised.
Signs that Your Phone Has Been Hacked
There are several signs that may indicate that your phone has been hacked. One common sign is unusual or unexpected behavior on your device, such as apps opening or closing on their own, or the device shutting down unexpectedly.
Another sign is an increase in data usage or unusual charges on your phone bill, which may indicate that someone is using your device without your knowledge.
Additionally, if you notice that your contacts or messages have been deleted or altered, this may be a sign that your phone has been hacked.
Other signs include a decrease in battery life, unusual pop-ups or notifications, and changes to your device’s settings or home screen.
If you suspect that your phone has been hacked, it is important to take immediate action, such as resetting your device, changing your passwords, and contacting your mobile service provider. By taking swift action, you can minimize the damage caused by a phone hack and protect your personal and sensitive information.
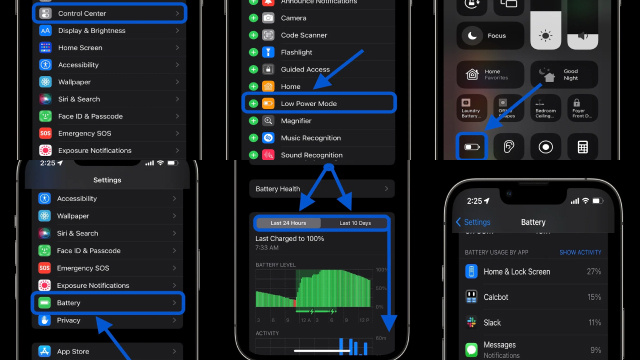
Battery Life and Temperature Changes
Changes in battery life and temperature can be signs that your device has been compromised or hacked. Malware and other types of malicious software can cause your device to consume more battery power than usual, resulting in decreased battery life.
In addition, malware can cause your device to overheat, leading to physical damage and potential safety hazards.
If you notice that your device’s battery life is decreasing rapidly or that it is getting unusually hot, it is important to investigate the cause. This may involve running a virus scan on your device, checking for unauthorized apps or software, and making sure that your device’s software and security features are up to date.
By taking action to identify and address the cause of battery life and temperature changes, you can help to protect your device from cyber threats and ensure that it continues to function properly.
Increased Data Usage and Charges
Increased data usage and charges on your mobile phone bill can be a sign that your device has been compromised or hacked. Hackers may use your device to perform activities that require a lot of data, such as downloading large files or streaming video content.
In addition, some types of malware may cause your device to send or receive data without your knowledge, resulting in increased data usage and charges.
If you notice an unexplained increase in data usage or charges on your phone bill, it is important to investigate the cause. This may involve running a virus scan on your device, checking for unauthorized apps or software, and changing your passwords.
By taking action to identify and address the cause of increased data usage and charges, you can help to protect your personal and financial information from cybercriminals.
Unusual Pop-Ups and Advertisements
Unusual pop-ups and advertisements on your device can be a sign that your device has been compromised or hacked. Hackers often use these types of tactics to trick users into clicking on malicious links or downloading harmful software.
If you notice that your device is displaying pop-ups or advertisements that are unrelated to the apps or websites you are using, or that are particularly aggressive or intrusive, it is important to investigate the cause.
One way to address this issue is to install an ad-blocker or pop-up blocker on your device. These tools can help to prevent unwanted ads and pop-ups from appearing on your screen.
In addition, it is important to avoid clicking on suspicious links or downloading software from untrusted sources. Always make sure to download apps and software from reputable sources, such as the Apple App Store or Google Play Store, and to read user reviews and ratings before downloading.
By taking steps to prevent and address unusual pop-ups and advertisements on your device, you can help to protect your personal and sensitive information from cybercriminals and maintain the security of your device.
Apps That You Didn’t Install
If you notice apps on your device that you didn’t install, it could be a sign that your device has been compromised or hacked. Malicious software or other types of cyber threats can install unwanted apps on your device without your knowledge or consent.
It is important to investigate the cause of these unauthorized apps and take action to remove them from your device. This may involve running a virus scan or malware removal tool, checking for any unauthorized changes to your device’s settings, and reviewing your device’s app permissions.
In addition, it is important to avoid downloading apps from untrusted sources and to only download apps from reputable app stores, such as the Apple App Store or Google Play Store.
By taking steps to address unauthorized apps on your device, you can help to protect your personal and sensitive information from cybercriminals and maintain the security of your device.
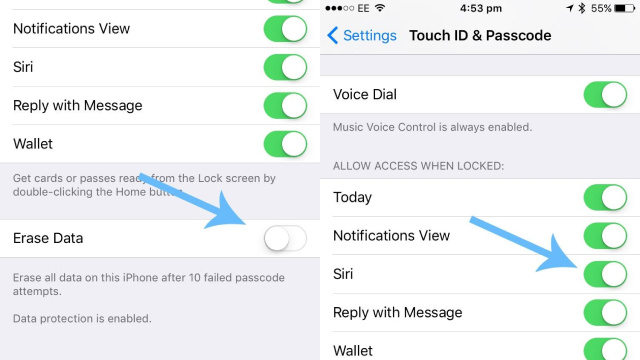
Suspicious Activity on Your Accounts
If you notice suspicious activity on your accounts, such as unauthorized transactions, logins from unfamiliar locations, or changes to your account information, it could be a sign that your accounts have been compromised or hacked.
It is important to take immediate action to secure your accounts and prevent further unauthorized access. This may involve changing your passwords, enabling two-factor authentication, or contacting your financial institution or service provider to report the suspicious activity.
In addition, it is important to regularly monitor your accounts for any signs of suspicious activity and to review your account settings and security features to ensure they are up to date and effective.
By taking steps to address suspicious activity on your accounts, you can help to protect your personal and financial information from cybercriminals and maintain the security of your accounts.
Protecting Your Phone from Hackers
Protecting your phone from hackers is crucial to ensure the security of your personal information and prevent unauthorized access to your device. Here are some steps you can take to protect your phone from hackers:
- Use strong passwords and enable two-factor authentication: Create strong, unique passwords for your phone and enable two-factor authentication for added security.
- Keep your software up to date: Regularly update your phone’s operating system and apps to ensure that they have the latest security patches and bug fixes.
- Be cautious of public Wi-Fi networks: Avoid using public Wi-Fi networks as they may be unsecured and make your device vulnerable to hacking.
- Use a Virtual Private Network (VPN): If you must use public Wi-Fi, consider using a VPN to encrypt your online activity and protect your device from hackers.
- Be wary of suspicious links and downloads: Avoid clicking on suspicious links or downloading software from untrusted sources, as they may contain malware or other types of cyber threats.
By taking these steps, you can help to protect your phone from hackers and maintain the security of your personal information. Remember to stay vigilant and take action if you suspect that your device has been compromised.