Understanding Phishing Scams: How to Protect Yourself Online
In today’s digital age, online security has become paramount. One of the most prevalent threats users face is phishing scams. Phishing scams are deceptive attempts by cybercriminals to trick individuals into revealing sensitive information such as passwords, credit card details, or social security numbers. Understanding the inner workings of phishing scams is crucial for protecting yourself online.
Phishing scams often come in the form of emails, text messages, or even phone calls that appear to be from reputable sources like banks, government agencies, or popular online platforms. These messages usually employ urgent or alarming language, aiming to create a sense of urgency and coerce recipients into taking immediate action.
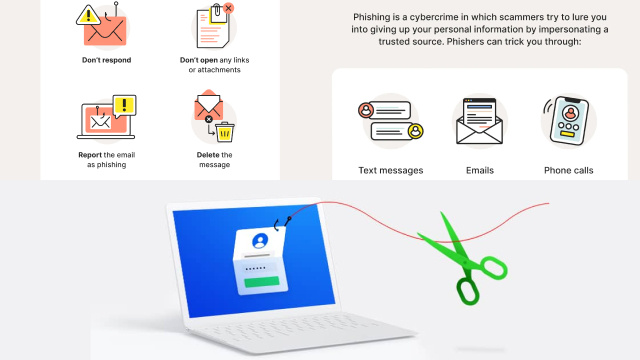
To protect yourself from phishing scams, it’s essential to cultivate a skeptical mindset. Be cautious of unsolicited messages, especially those requesting personal information or urging you to click on suspicious links. Instead of directly clicking on links, manually type the URL of the website in question to ensure authenticity.
Another effective measure is to regularly update and strengthen your passwords. Opt for unique, complex passwords and enable two-factor authentication whenever possible. Additionally, keeping your devices and software up to date with the latest security patches adds an extra layer of protection.
Remember, vigilance is key when it comes to combating phishing scams. By staying informed and adopting proactive security measures, you can navigate the digital landscape with confidence and protect yourself from falling victim to these malicious schemes.
The Anatomy of Phishing Scams: Tactics and Techniques Unveiled
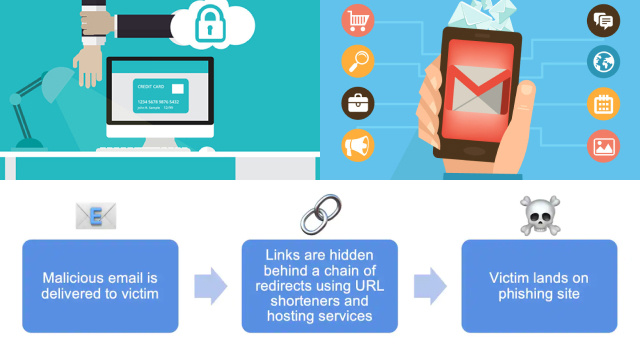
Phishing scams are sophisticated maneuvers crafted by cybercriminals to deceive unsuspecting individuals. Understanding the anatomy of these scams is crucial to recognizing and avoiding them. Phishing tactics often involve creating a false sense of urgency or fear, compelling recipients to take immediate action. Techniques such as email spoofing, where the sender’s address is manipulated to appear legitimate, and website spoofing, where fake websites mimic reputable ones, are commonly employed. Additionally, social engineering techniques are used to manipulate emotions and trick users into divulging sensitive information. By shedding light on the tactics and techniques employed by phishing scams, we can empower ourselves to stay vigilant and protect our online identities.
Stay One Step Ahead: Tips to Recognize and Avoid Phishing Scams
In the digital landscape, staying one step ahead of phishing scams is crucial to safeguarding your online security. By familiarizing yourself with key tips to recognize and avoid these scams, you can protect yourself from falling victim to cybercriminals. Firstly, scrutinize suspicious emails or messages, paying attention to grammar mistakes, generic greetings, or unexpected requests for personal information. Secondly, avoid clicking on unfamiliar links or downloading attachments from untrusted sources. Instead, independently verify the legitimacy of the sender or website.
Lastly, keep your devices and software up to date, utilize strong, unique passwords, and enable two-factor authentication whenever possible. By staying informed and practicing caution, you can proactively defend against phishing scams and maintain your online safety.
Phishing Scams Exposed: Common Red Flags to Watch Out For
Phishing scams continue to evolve, but they often exhibit common red flags that can help you identify and avoid falling into their traps. One major red flag is receiving unsolicited emails or messages requesting sensitive information like passwords or credit card details. Be cautious of urgent or threatening language, as cybercriminals often use fear to coerce their victims. Poor grammar, spelling mistakes, or generic greetings can also indicate a phishing attempt. Additionally, be wary of suspicious links or attachments, especially if they come from unknown sources. Legitimate organizations rarely ask you to click on links to verify personal information. By staying vigilant and recognizing these red flags, you can protect yourself from phishing scams and keep your personal information secure.
The Growing Threat: Exploring the Rise of Sophisticated Phishing Scams
In recent years, we have witnessed a concerning trend in the realm of online security: the rise of sophisticated phishing scams. Cybercriminals have honed their tactics and techniques, making these scams more convincing and harder to detect. One reason for their growing prevalence is the increasing reliance on digital communication and transactions. Phishing scams often target individuals through emails, text messages, or even social media platforms, posing as legitimate entities such as banks, online retailers, or government agencies. They exploit human vulnerabilities, employing psychological manipulation to trick victims into divulging personal information or clicking on malicious links.
As technology advances, phishing scams become more intricate, with attackers employing advanced spoofing techniques and utilizing compromised websites. To combat this growing threat, it is crucial to stay informed, exercise caution, and employ robust security measures to protect oneself from falling victim to these sophisticated phishing scams.
Don’t Take the Bait: Best Practices for Defending Against Phishing Attacks
In the digital landscape, phishing attacks pose a significant threat to online security. To defend against these deceptive tactics, it is crucial to adopt best practices that can help you avoid falling victim to such attacks. Firstly, be vigilant and skeptical of unsolicited emails, messages, or phone calls asking for personal information. Verify the legitimacy of the sender by independently contacting the organization through official channels. Secondly, scrutinize URLs and avoid clicking on suspicious links. Hover over the link to preview the destination and ensure it matches the context of the message. Thirdly, fortify your defenses with robust security software, including anti-phishing tools and firewalls. Regularly update your software to stay protected against the latest threats. Lastly, educate yourself and your colleagues about phishing techniques and encourage a culture of security awareness. By staying alert and implementing these best practices, you can effectively defend against phishing attacks and safeguard your online presence.
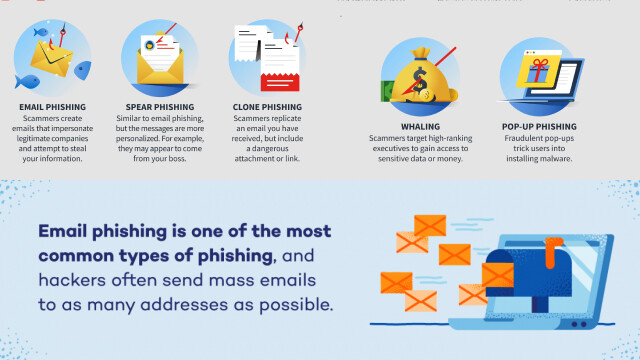
Beyond Emails: Uncovering Different Forms of Phishing Scams
While emails are commonly associated with phishing scams, it is important to recognize that cybercriminals have expanded their repertoire beyond this traditional method. Phishing attacks can now be found in various forms across different communication channels. One prominent example is smishing, where fraudsters send malicious text messages that appear to be from legitimate sources, urging recipients to take immediate action or providing links to fake websites. Another form is vishing, which involves voice-based phishing scams where scammers impersonate trusted organizations over phone calls, tricking victims into revealing sensitive information.
Additionally, there are social media phishing scams, where cybercriminals create fake profiles or pages to deceive users into sharing personal data or clicking on malicious links. It is crucial to stay informed about these evolving tactics and remain cautious across all communication platforms. By recognizing the different forms of phishing scams, we can enhance our defenses and protect ourselves from falling victim to these deceptive schemes.
Building a Secure Shield: Essential Tools and Strategies to Combat Phishing Scams
In the relentless battle against phishing scams, building a secure shield is essential to protect yourself and your sensitive information. Fortunately, there are various tools and strategies available that can significantly enhance your defense against these malicious attacks.
Firstly, it is crucial to invest in robust antivirus and anti-malware software. These tools act as a frontline defense, constantly scanning and detecting potential threats, including phishing attempts. Regularly update these programs to ensure they are equipped with the latest security measures.
Secondly, enable multi-factor authentication (MFA) whenever possible. MFA adds an extra layer of protection by requiring multiple forms of verification, such as a password and a unique code sent to your mobile device. This makes it significantly harder for cybercriminals to gain unauthorized access to your accounts.
Another effective strategy is to educate yourself and your team about phishing techniques and common red flags. By being aware of the latest trends in phishing scams, you can recognize suspicious emails, messages, or websites more easily. Teach yourself to spot signs of urgency, poor grammar, unexpected requests for personal information, or mismatched URLs.
Furthermore, consider implementing email filtering and spam detection systems. These tools can automatically detect and block potential phishing emails, reducing the risk of them reaching your inbox. Regularly update and fine-tune these systems to ensure their effectiveness.
Lastly, cultivate a healthy dose of skepticism. Treat all unsolicited messages with caution, especially those requesting personal information or urging immediate action. Instead of clicking on links directly, manually type the URL of the website in question. Verify the legitimacy of the sender through official channels before sharing any sensitive information.
By combining these essential tools and strategies, you can construct a robust shield against phishing scams. Remember, staying proactive and continuously updating your security measures is key to mitigating the risks and protecting yourself in the ever-evolving landscape of cyber threats.