With growing internet surveillance, scam websites, and many other cyber risks, it’s evident that the internet is never safe. Consequently, consumers are taking measures to protect their online browsing. An increasing number of consumers are now using VPN tunnels to connect to the internet safely. However, there’s a lot of confusion around VPN tunneling, how VPN works, and whether VPNs are reliable. Read on to learn more about VPNs and the tunneling process.
What is a VPN Tunnel?
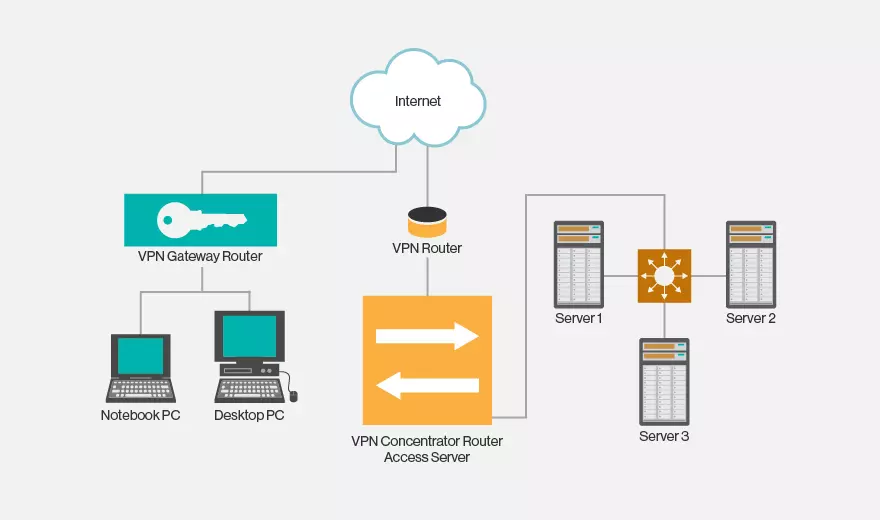
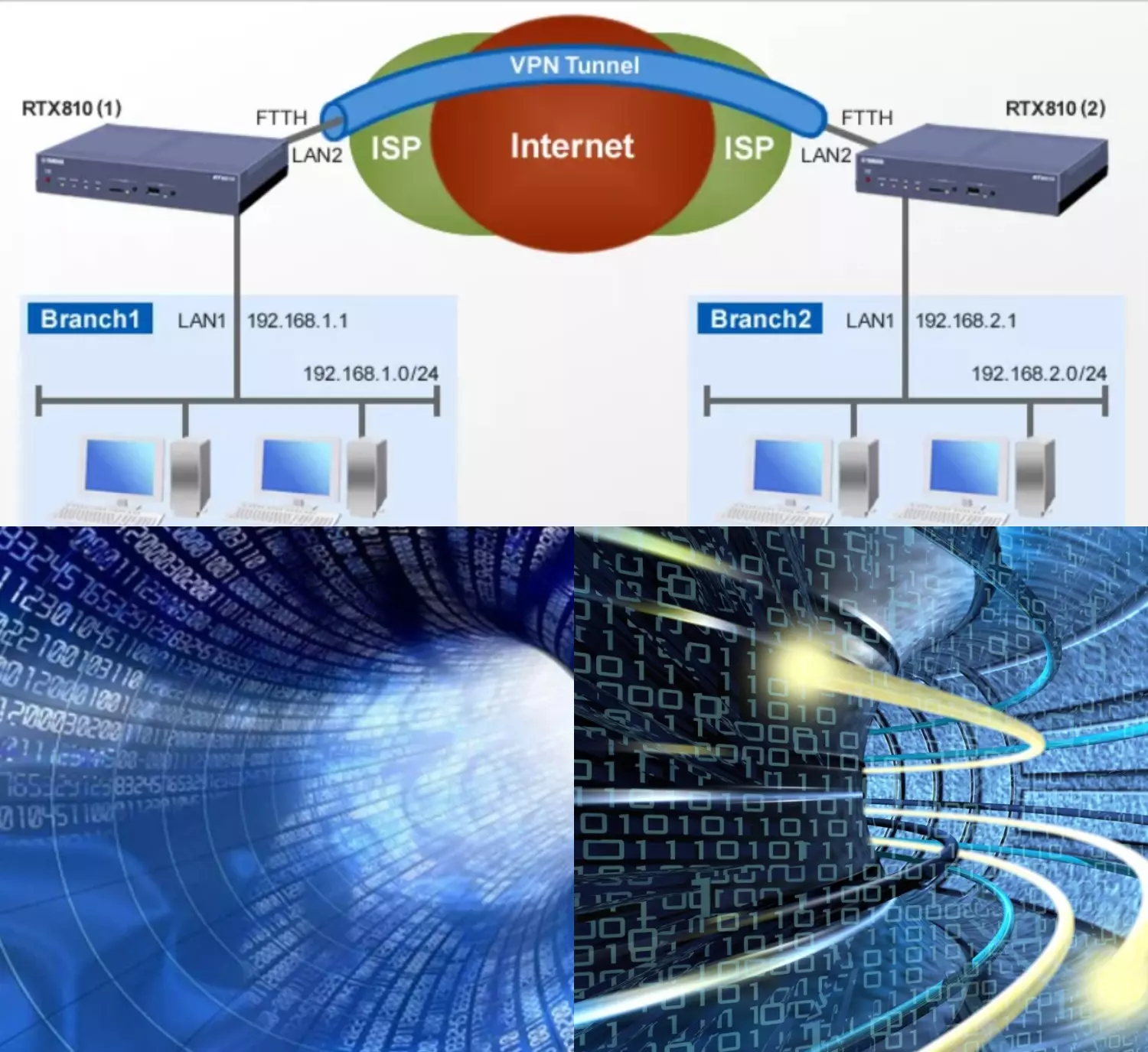
A network tunnel, also known as virtual private network tunnel is an encrypted connection between your device and the wider internet. Basically, it encrypts data and keeps it separate from other traffic on the internet. Encryption transforms data packets into unreadable form making it impossible for snoops to read the contents. The encrypted data is decrypted into readable form when it reaches its end destination. The tunneling process ensures nobody along the tunnel can intercept your communications since your connection is encrypted. A secure tunnel prevents sniffers from tracking your online activity, viewing your IP address, or identifying your location while online. A network tunnel guarantees the confidentiality and integrity of data as it traverses a public network.
How does a VPN tunnel work?
A virtual private network tunnel encapsulates and encrypts data packets as they travel between your device and a VPN server. Encapsulation separates data packets from other data traveling over the same network while encryption makes it unreadable. Another point in the VPN network decrypts the data, making it readable, and sends it to the end destination. When data packets traveling over a VPN network are encrypted, sniffers can’t intercept or decipher it. Malicious attackers won’t be able to track your online browsing when you tunnel your connection using a secure VPN.
Why use a VPN tunnel?
Browse the web securely
The internet is full of malicious snoops whose aim is to steal your personal data for malicious purposes. An internet tunnel guarantees online security by encrypting your connection to remove all chances of spying on your data. VPN tunneling protocols hide your IP address and location and make it hard for hackers to intercept your data.
Bypass censorship
Oppressive regimes around the world prevent their citizens from accessing certain websites. With a tunneling connection, you can easily bypass oppressive government censorship and access websites that are unavailable in your country.
Online anonymity
VPN tunnel encryption hides your IP and allows you to access the internet from different location servers. This anonymity protects you from cyberattacks and scam websites.
Beat location-based streaming restrictions
Streaming services like Netflix limit access to their content for some users based on geographical location. With VPN tunneling encryption, you can bypass these location-based restrictions. Whether you want to access Netflix US or BBC iPlayer from outside the U.S or UK, VPN tunneling can help.
Save money shopping online
Online shopping sites offer different prices for the same item for customers from different countries. With VPN tunneling, you can beat this location bias and get the best deals at the best rates.
Types of VPN tunnels
What is VPN tunneling protocol?
VPN tunneling protocol refers to a kind of communications protocol designed to create a tunnel between two points on a network. This protocol helps to securely transmit data between the two points.
The most reliable VPN service providers rely on four major types of tunneling protocols. They include:
OpenVPN
OpenVPN is considered one of the most secure protocols. It’s based upon a secure sockets layer (SSL) for its encryption protocol. It’s compatible with all major operating systems.
IPSec/IKEv2
This VPN tunneling protocol combines IPSec (internet protocol security suite) and IKEv2 (Internet key exchange version two). The VPN protocol is considerably secure and supports fast VPN connections.
WireGuard
This is a new VPN tunneling protocol that utilizes advanced cryptography and algorithms to offer better security. WireGuard boasts faster speeds, ease of use, and compatibility with all the major operating systems.
SSTP
SSTP, or secure socket tunneling protocol transmits PPP traffic through a secure sockets layer or SSL, or TSL channel. It uses strong encryption procedures to create a secure connection with your device. SSTP is only compatible with Windows.
What is split tunneling?
Split tunneling is simply the splitting of internet traffic. Some internet traffic is sent through a VPN tunnel while leaving the rest of the traffic to access the internet directly. Split tunneling allows you to control your internet traffic and gives you extra security without sacrificing speed.
Conclusion
A VPN tunnel is an indispensable tool when it comes to online privacy and freedom. Nobody can snoop into your browsing activity when your connection is encrypted with a reliable VPN tunnel. The reliability of your VPN depends on your choice of tunneling protocol. Be sure to choose a VPN that uses the best tunneling protocol.