Introduction to Digital Footprints: What They Are and How They Work
A digital footprint is the trail of data and information that a person leaves behind online. This includes any information that is created, shared, or accessed through the internet, such as social media posts, online purchases, and search history.
Digital footprints are created through a variety of methods, including cookies and tracking technologies that are used by websites and advertisers to collect data about users. This data can be used to create targeted advertising and personalized content, but can also be used to track user behavior and activities.
Digital footprints can have both positive and negative impacts on individuals and organizations. On the one hand, a strong and positive digital footprint can help build a personal brand or establish credibility. On the other hand, a negative digital footprint can harm a person’s reputation and limit their opportunities.
Understanding digital footprints and how they work is critical for individuals and organizations to protect their online privacy and reputation. By being mindful of the data they share online and taking steps to control their digital footprint, individuals can help ensure that their online presence is a positive reflection of themselves or their organization.
Types of Digital Footprints: Active and Passive
There are two types of digital footprints: active and passive. Active digital footprints are created intentionally by individuals when they post content online, such as social media posts, blog articles, and comments on websites. These footprints can be used to build a personal brand or promote a business.
Passive digital footprints, on the other hand, are created unintentionally through the use of technology and the internet. These footprints can include browsing history, search queries, and cookies that track user behavior and interests. This information can be used by advertisers and other third parties to create targeted advertising and personalized content.
Both active and passive digital footprints can have significant impacts on individuals and organizations. Positive digital footprints can help build credibility and establish a strong online presence, while negative footprints can harm reputation and limit opportunities. It is important for individuals and organizations to be aware of the types of digital footprints they are creating and take steps to manage their online presence accordingly.
Components of a Digital Footprint: Personal Information, Online Activity, and Data Trails
A digital footprint is made up of several components, including personal information, online activity, and data trails. Personal information includes any data that can identify an individual, such as their name, address, phone number, and email address. This information can be found in various online platforms, such as social media, online directories, and public records.
Online activity includes any actions that an individual takes online, such as browsing history, search queries, and social media posts. This information can be used to build a profile of the individual’s interests and behaviors, which can then be used for targeted advertising or other purposes.
Data trails refer to the traces that an individual leaves behind when they use technology and the internet, such as cookies, IP addresses, and device information. These data trails can be used to track user behavior and preferences, which can then be used for advertising and other purposes.
Overall, understanding the components of a digital footprint is essential for individuals and organizations to protect their online privacy and reputation. By being aware of the personal information, online activity, and data trails they are leaving behind, individuals can take steps to manage their digital footprint and control how their information is used online.
Risks of a Digital Footprint: Identity Theft, Cyberstalking, and Social Engineering
A digital footprint can expose individuals to a range of risks, including identity theft, cyberstalking, and social engineering. Identity theft occurs when an individual’s personal information is stolen and used for fraudulent purposes, such as opening credit accounts or filing tax returns.
Cyberstalking involves the use of technology to track and harass individuals, often through social media or email. This can lead to emotional distress and even physical harm.
Social engineering involves the manipulation of individuals to gain access to sensitive information, such as passwords or financial data. This can be done through tactics such as phishing emails or impersonation scams.
Overall, the risks of a digital footprint highlight the importance of online privacy and security. Individuals can protect themselves by being mindful of the information they share online, using strong passwords, and being cautious of suspicious emails or messages. Organizations can also take steps to protect customer data and implement security measures to prevent data breaches.
How Hackers Exploit Digital Footprints: Phishing, Social Engineering, and Data Mining
Hackers can exploit digital footprints in several ways, including phishing, social engineering, and data mining. Phishing involves the use of fake emails or websites to trick individuals into sharing sensitive information, such as login credentials or financial data. This can be done by impersonating a trusted entity, such as a bank or social media platform.
Social engineering involves manipulating individuals into divulging sensitive information through psychological tactics, such as building trust or creating a sense of urgency. This can be done through phone calls, emails, or social media messages.
Data mining involves collecting and analyzing data from various sources, such as social media and public records, to build a profile of an individual and identify potential vulnerabilities. This information can then be used to launch targeted attacks, such as spear phishing or ransomware attacks.
Overall, hackers can use digital footprints to gain access to sensitive information and launch targeted attacks. Individuals and organizations can protect themselves by being aware of these tactics and taking steps to secure their online presence, such as using strong passwords, enabling two-factor authentication, and being cautious of suspicious messages or websites.
Best Practices for Protecting Your Digital Footprint: Strong Passwords, Two-Factor Authentication, and Privacy Settings
Protecting your digital footprint is crucial in today’s world of constant online activity. Some best practices for safeguarding your digital presence include using strong passwords, enabling two-factor authentication, and adjusting your privacy settings on social media platforms.
Strong passwords are essential for securing online accounts. Use a mix of upper and lowercase letters, numbers, and symbols, and avoid using easily guessable information, such as your birthdate or pet’s name.
Two-factor authentication adds an extra layer of security by requiring a second form of authentication, such as a text message or fingerprint scan, in addition to your password.
Privacy settings on social media platforms can help control who sees your personal information and posts. Adjust these settings to limit access to your content and prevent unauthorized sharing.
Overall, taking these steps can help protect your digital footprint and safeguard your personal information online. Stay vigilant and regularly update your security measures to stay ahead of potential threats.
Tools and Technologies for Monitoring and Managing Your Digital Footprint: VPNs, Browser Extensions, and Privacy Services
There are several tools and technologies available to monitor and manage your digital footprint, including virtual private networks (VPNs), browser extensions, and privacy services.
VPNs provide a secure and encrypted connection between your device and the internet, masking your IP address and online activity from potential eavesdroppers. This can help protect your privacy and prevent unauthorized access to your data.
Browser extensions, such as ad-blockers and tracker-blockers, can help limit the amount of data collected about you as you browse the web. These extensions block third-party cookies and prevent websites from tracking your online behavior.
Privacy services, such as identity theft protection and credit monitoring, can help monitor your personal information and alert you to potential risks, such as unauthorized access to your financial accounts.
By using these tools and technologies, you can better manage your digital footprint and protect your online privacy. Be sure to research and choose reputable services and regularly update your security measures to stay ahead of potential threats.
Legal and Ethical Considerations of Digital Footprints: Data Privacy, Surveillance, and Cybercrime
The use of digital footprints raises important legal and ethical considerations, including data privacy, surveillance, and cybercrime.
Data privacy laws, such as the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States, aim to protect individuals’ personal information and give them greater control over how their data is collected, processed, and shared.
Surveillance and monitoring of digital footprints by governments and corporations raise concerns about civil liberties and the potential abuse of power. The use of this data for purposes such as targeted advertising or law enforcement can also have ethical implications.
Cybercrime, such as identity theft and online fraud, also pose a significant threat to individuals’ digital footprints and can have serious legal and financial consequences.
As individuals, it’s important to be aware of these legal and ethical considerations and take steps to protect our digital footprints, such as using strong passwords and enabling two-factor authentication. It’s also important for lawmakers and businesses to consider these issues when developing policies and practices related to digital footprints.
Educating the Next Generation: Teaching Children and Teens about Digital Footprint Protection
In today’s digital age, it’s crucial to instill an understanding of digital footprint protection in children and teenagers. A digital footprint is the trail of data left behind by online activities, and educating the younger generation about its significance is essential for their online safety and privacy.
The Importance of Digital Footprint Education:
- Early Exposure: Children are increasingly exposed to the digital world from a young age. Teaching them about digital footprints early helps them make informed choices about their online behavior.
- Long-Term Impact: The data shared online can have lasting consequences. It’s crucial for young people to grasp that their digital actions can affect their future, including college admissions and job opportunities.
- Online Safety: Understanding digital footprints can make children and teens more aware of online risks, such as cyberbullying, identity theft, and the importance of privacy.
Key Aspects of Digital Footprint Education:
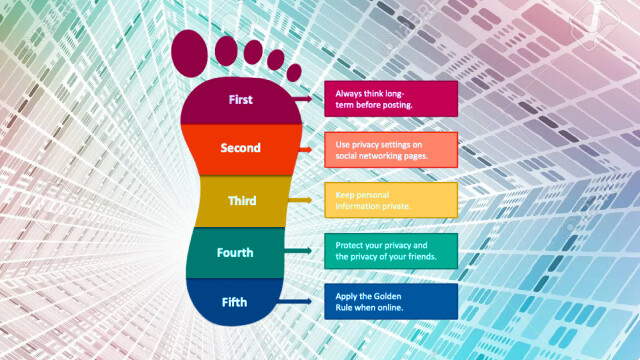
- Online Behavior: Teach responsible online behavior, including the significance of not oversharing personal information and being mindful of what they post.
- Privacy Settings: Show them how to adjust privacy settings on social media platforms and other online accounts to control who can see their information.
- Cybersecurity: Explain the importance of strong, unique passwords and the use of two-factor authentication to protect accounts.
- Critical Thinking: Encourage critical thinking and skepticism, helping them identify and avoid online scams and fake information.
- Respect and Empathy: Promote respectful online communication and empathy to combat cyberbullying and harassment.
Parental Involvement:
Parents play a vital role in this education. They should lead by example, create open lines of communication, and be a resource for their children when they encounter online challenges or have questions about digital footprints.
Conclusion: Balancing Online Convenience and Security to Protect Your Digital Footprint
In today’s digital age, our digital footprints are increasingly important and require attention to ensure privacy and security. While it’s convenient to have all our personal information and online activity in one place, it also creates potential risks, such as identity theft, cyberstalking, and surveillance.
To protect our digital footprints, we need to balance convenience and security. This means taking steps such as using strong passwords, enabling two-factor authentication, and regularly monitoring our online activity.
It’s also important to be aware of the legal and ethical considerations related to digital footprints and advocate for policies and practices that protect our privacy and civil liberties.
By taking a proactive approach to our digital footprints, we can enjoy the benefits of online convenience while minimizing the potential risks. Remember to regularly update your security measures and stay informed about the latest developments in data privacy and cybersecurity.