Understanding ISP Tracking: Can Your ISP See Your Browsing History?
When you browse the internet, your Internet Service Provider (ISP) is responsible for providing you with access to websites and transferring data between your device and the internet. However, many people are concerned about whether their ISP can see their browsing history and track their online activities.
The short answer is yes, your ISP can see your browsing history. In fact, ISPs are required by law to collect certain information about their users, including their browsing history. This data can be used for a variety of purposes, such as targeted advertising, improving service quality, and monitoring for illegal activities.
To protect your privacy and prevent your ISP from seeing your browsing history, you can take several steps:
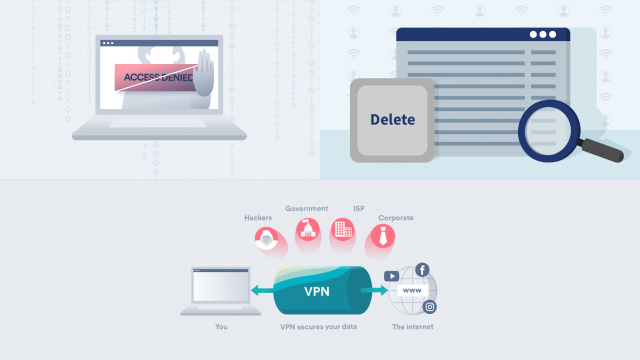
- Use a Virtual Private Network (VPN): A VPN encrypts your internet traffic, masking your IP address and preventing your ISP from monitoring your online activities. By routing your connection through a secure server, a VPN ensures that your browsing history remains private. Choose Planet VPN with a no-logs policy to maximize security and privacy.
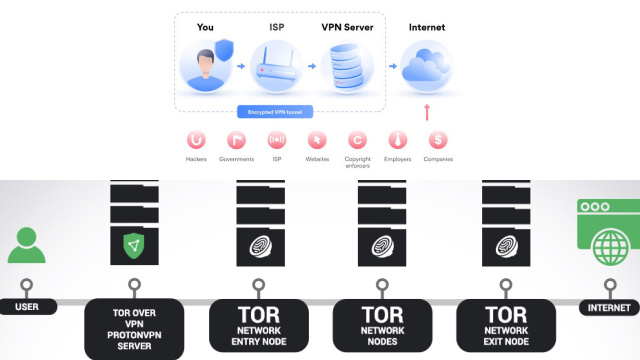
- Use Tor: Tor is a free software that anonymizes your internet traffic by encrypting it. This process hides your IP address and makes it nearly impossible for your ISP or other third parties to track your online activities. While Tor is highly effective for anonymity, it may reduce your browsing speed.
You might be interested in: Tor vs VPN: What’s the Difference and Which Is Better in 2024?
Ultimately, it’s important to understand the risks of ISP tracking and take steps to protect your online privacy.
The Legal Landscape: What Regulations Govern ISP Data Collection?
The collection of data by Internet Service Providers (ISPs) is governed by various laws and regulations, both at the national and international levels.
- In the United States, the Federal Communications Commission (FCC) has established rules that require ISPs to obtain opt-in consent from their users before collecting and sharing sensitive information, such as browsing history and app usage data.
- Additionally, the European Union’s General Data Protection Regulation (GDPR) regulates the collection and processing of personal data by ISPs and other entities, and provides individuals with certain rights over their data, such as the right to access and delete their information.
- Other countries also have their own laws and regulations governing ISP data collection, and there are ongoing debates about the appropriate balance between privacy and the needs of law enforcement and national security.
Understanding these regulations is crucial for individuals who want to protect their online privacy and limit the amount of data that ISPs collect about them.
What Your ISP Collects: A Closer Look at the Data They Gather
Internet Service Providers (ISPs) collect a variety of data about their users, including:
- Browsing history – Sites visited and online activity.
- IP addresses – Identifying users’ network locations.
- Device information – Details about connected devices.
- Location data – Tracking user locations.
- App & website usage – Monitoring accessed platforms.
- Downloaded & streamed content
This information can be used for a variety of purposes, such as:
- Enhancing service quality.
- Delivering targeted ads.
- Detecting and preventing illegal activities.
However, many people are concerned about the potential misuse of this data and the invasion of their privacy.
To address these concerns, some ISPs have implemented privacy policies that outline what data they collect and how it is used.
Additionally, users can take steps to protect their privacy by:
- Using a VPN or Tor to encrypt traffic and mask IP addresses.
- Understanding ISP policies to staying informed about data collection practices.
By being aware of ISP tracking, users can take steps to safeguard their privacy and limit data exposure.
The Risks of ISP Tracking: How Your Browsing History Could Be Used Against You
1. Data Collection:
Internet Service Providers (ISPs) collect and store a significant amount of data about their users, including browsing history and app usage data.
While this information is used for a variety of purposes, such as improving service quality and delivering targeted advertising, there are also risks associated with ISP tracking.
2. Potential misuse of data by ISPs or other third parties:
Browsing history, for example, can reveal a significant amount of personal information, such as political views, health concerns, and financial information.
This data can be used to target individuals with advertising, or even to discriminate against them in areas such as employment or housing.
3. Government Access:
ISPs may be required to provide access to user data to law enforcement or government agencies, which can lead to privacy violations and potentially even legal repercussions for individuals.
Individuals need to understand the risks associated with ISP tracking and take steps to protect their online privacy.
Protecting Your Privacy: Tips for Keeping Your Browsing History Private
Protecting your online privacy is becoming increasingly important in today’s digital age. To keep your browsing history private, there are several steps you can take.
- VPN or Tor: One of the most effective ways to protect your privacy is to use a Virtual Private Network (VPN) or Tor to encrypt your internet traffic and hide your IP address.
- Privacy-focused browser: Another option is to use a privacy-focused browser, such as Mozilla Firefox or Brave, which offers built-in privacy protections.
- Unique passwords: in addition, it’s important to be cautious about the information you share online and to use strong, unique passwords for all of your accounts.
You can also adjust the settings on your browser to limit the amount of data that is collected about you. For example, you can disable cookies, use browser extensions that block trackers, and clear your browsing history regularly.
By taking these steps, you can help to protect your online privacy and keep your browsing history private.
Using VPNs and Tor: How These Tools Can Help You Stay Anonymous Online
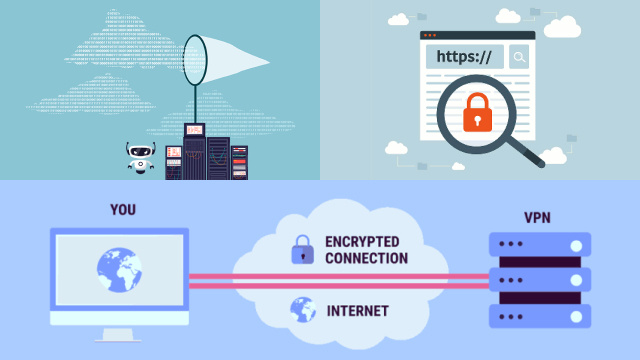
Virtual Private Networks (VPNs) and Tor are two tools that can help you stay anonymous online by encrypting your internet traffic and masking your IP address.
VPNs: work by routing your internet traffic through a remote server, which encrypts the data and hides your IP address. This makes it difficult for ISPs and other third parties to track your online activity.
Tor: is a browser that uses a series of encrypted relays to mask your IP address and keep your online activity private.
Both VPNs and Tor have their advantages and disadvantages, so selecting the right tool depends on your specific needs.
- VPNs offer better speed and are ideal for general privacy and bypassing geo-restrictions.
- Tor provides stronger anonymity but can be slower due to multiple encryption layers.
While these tools enhance privacy, they are not foolproof. It’s crucial to follow good security practices, such as using strong passwords and being mindful of the information you share online.
The Future of ISP Tracking: Will New Technologies Change the Game?
The internet landscape is constantly evolving, and new technologies are emerging that may have a significant impact on ISP tracking.
- Privacy Enhancements – Technologies like encrypted DNS and HTTPS make it harder for ISPs to monitor browsing activity.
- New Tracking Methods – Techniques such as browser fingerprinting and device tracking can identify users even when using VPNs or Tor.
These technologies can be used to identify individual users based on the unique characteristics of their device or browser, even if they are using a VPN or Tor.
It’s unclear how these new technologies will impact the future of ISP tracking, but the landscape will likely continue to evolve.
As a result, individuals need to stay informed about the latest developments in online privacy and take steps to protect their personal information. This may include using privacy-focused browsers and VPNs, as well as being cautious about the information you share online.
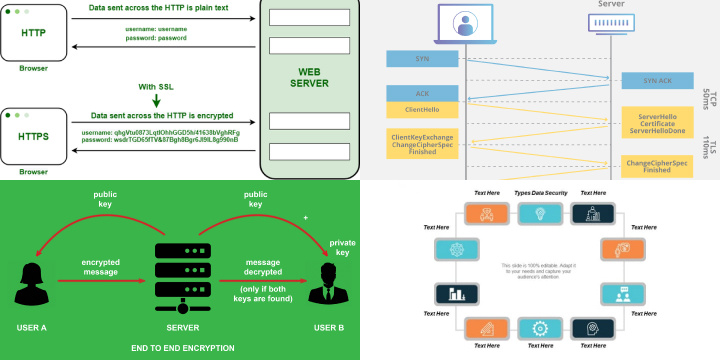
Encrypted Browsing: How HTTPS and Secure Connections Shield Your Data from ISPs
Encrypted browsing, primarily facilitated through HTTPS (Hypertext Transfer Protocol Secure) and secure connections, plays a crucial role in shielding your data from ISPs (Internet Service Providers) and potential eavesdroppers. Here’s how it works:
- HTTPS Encryption: When you access a website with HTTPS, your data is encrypted before being transmitted. This encryption ensures that even if your ISP intercepts the data, they can’t decipher its contents.
- SSL/TLS Protocols: HTTPS relies on SSL (Secure Sockets Layer) or TLS (Transport Layer Security) protocols to establish a secure connection between your device and the website’s server. This secure “handshake” encrypts data in transit.
- Data Integrity: HTTPS not only encrypts data but also ensures its integrity. It uses checksums and digital signatures to detect and prevent data tampering during transmission.
- End-to-End Encryption: Messaging apps like WhatsApp and Signal employ end-to-end encryption, which ensures that only the intended recipient can decrypt and read the messages, even if they pass through an ISP’s servers.
- Protecting Sensitive Information: Secure connections are crucial when transmitting sensitive data like credit card information or login credentials. HTTPS ensures this information remains confidential.
- Trust Indicators: Browsers display visual cues like padlock icons and “Secure” labels for HTTPS websites. These indicators help users identify secure connections.
- ISP Data Collection: While ISPs can still see the domains you visit, they can’t access the specific content of encrypted connections, enhancing your online privacy.
- Browser Extensions: Privacy-focused browser extensions like HTTPS Everywhere automatically force HTTPS connections when available, further securing your browsing.
In summary, encrypted browsing, especially through HTTPS and secure connections, forms a critical defense against ISP data monitoring and potential threats. It ensures your online activities remain private and protected, enhancing your overall cybersecurity and data privacy.
Conclusion: Taking Control of Your Online Privacy
In today’s digital age, online privacy is more important than ever. With ISPs collecting and storing large amounts of data about their users, it’s essential to take steps to protect your personal information.
Fortunately, there are a variety of tools and techniques that can help you keep your browsing history private and stay anonymous online. From using VPNs and Tor to adjusting your browser settings, there are many ways to take control of your online privacy.
By staying informed about the latest developments in online privacy and adopting good security practices, you can help to protect your personal information and stay safe online.
Whether you’re browsing the web for personal or professional reasons, it’s important to be vigilant and take steps to keep your online activity private.