Introduction to Cloud Security and its Importance
Cloud security is a set of procedures and technologies that protect data, applications, and infrastructure in the cloud from unauthorized access, theft, and data breaches. With the rapid adoption of cloud services, cloud security has become an essential aspect of cybersecurity. The importance of cloud security lies in the fact that cloud environments are highly vulnerable to cyber attacks, data leaks, and system breaches.
With the cloud, data is stored in remote servers that can be accessed from anywhere, making it more susceptible to security threats. Cloud security helps prevent unauthorized access, protects data integrity, and ensures compliance with regulatory standards. Additionally, it provides protection against cyber threats, such as malware, ransomware, and phishing attacks. Implementing strong cloud security measures is critical to ensure the safety and privacy of sensitive information in the cloud.
Threats to Cloud Security: Malware, Data Breaches, and Insider Threats
Cloud security is a critical concern for organizations that use cloud services to store and process their data. There are various types of threats to cloud security, including malware, data breaches, and insider threats. Malware is a common threat that can infect cloud systems and steal or destroy data. It can be introduced to the system through malicious emails, phishing attacks, or infected software. Data breaches are another significant threat to cloud security, where attackers gain unauthorized access to sensitive data stored in the cloud. This can result in financial losses, reputational damage, and legal penalties. Insider threats, where employees or contractors misuse their access to the system, can also pose a significant risk to cloud security. Preventing these threats requires a combination of technical measures, such as firewalls and antivirus software, as well as employee training and awareness programs to reduce the risk of human error or intentional misconduct.
Cloud Security Standards and Regulations
To address the risks and challenges associated with cloud security, several standards and regulations have been developed to ensure that cloud service providers (CSPs) implement effective security measures to protect customer data. One of the most widely adopted standards for cloud security is the ISO/IEC 27001, which provides a comprehensive framework for managing information security risks.
Other standards, such as the Cloud Security Alliance (CSA) Security, Trust, and Assurance Registry (STAR), provide a set of guidelines for assessing the security controls of CSPs. In addition to these standards, various regulations, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), impose specific requirements on CSPs to ensure the privacy and security of sensitive data. Adhering to these standards and regulations helps ensure that CSPs implement robust security measures to protect customer data and comply with relevant laws and regulations.
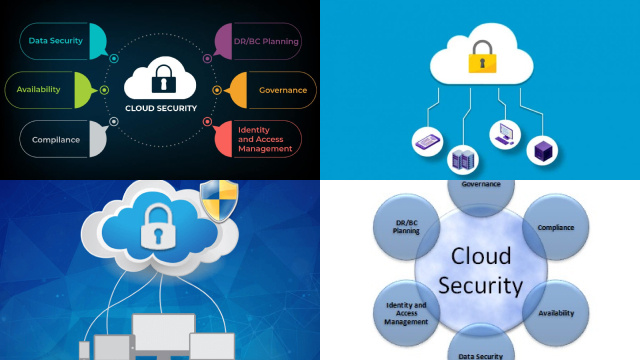
Key Elements of Cloud Security: Authentication, Authorization, and Encryption
Cloud security involves several key elements, including authentication, authorization, and encryption. Authentication is the process of verifying the identity of users or devices attempting to access a cloud system. It ensures that only authorized individuals can access sensitive data stored in the cloud. Authorization, on the other hand, involves granting users or devices access to specific resources based on their role or level of permission. It ensures that users can only access data and applications that are necessary for their work. Encryption is another critical element of cloud security, where data is encoded to protect it from unauthorized access or theft. It involves converting data into a cipher, which can only be deciphered using a secret key or password. These three elements of cloud security work together to ensure that data stored in the cloud is secure, and only authorized users can access it. Implementing strong authentication, authorization, and encryption measures is essential for safeguarding sensitive data and protecting against cyber threats.
Cloud Security Best Practices: Data Backup, Access Management, and Monitoring
Cloud security best practices involve a range of measures aimed at safeguarding data and systems in the cloud. One critical aspect of cloud security is data backup, where organizations ensure that all their data is regularly backed up to prevent loss in case of an attack or system failure. Access management is another crucial best practice that involves controlling who has access to cloud resources, including data and applications.
Organizations can use various tools such as multifactor authentication and identity and access management systems to ensure that only authorized users can access sensitive data. Monitoring is also essential for cloud security, where organizations continuously monitor their cloud systems for suspicious activities and vulnerabilities that could compromise their security. By implementing these cloud security best practices, organizations can protect their data and systems from cyber threats and ensure business continuity in case of an attack or system failure.
Public, Private, and Hybrid Cloud Security Considerations
Cloud computing offers different deployment models, each with unique security considerations. Public cloud services provide shared resources that are accessible over the internet, making them vulnerable to external threats. Organizations using public cloud services should ensure that they have robust security measures, such as data encryption and access controls, in place to protect their data from unauthorized access. Private cloud services, on the other hand, offer more control and security over the data and infrastructure, as they are accessible only to authorized users. However, managing a private cloud requires significant resources and expertise, making it more suitable for large enterprises. Hybrid cloud deployment models combine the benefits of both public and private clouds, allowing organizations to store sensitive data on-premise while leveraging public cloud services for less critical data. Managing security in a hybrid cloud environment requires integrating security policies and practices across both environments to ensure consistent protection. Organizations should consider their specific security requirements when selecting a cloud deployment model to ensure they choose the one that best suits their needs.
Risks and Challenges of Cloud Security: Vendor Lock-in, Lack of Transparency, and Data Sovereignty
As more and more businesses move their operations to the cloud, concerns about cloud security have become increasingly important. Three of the most significant risks and challenges facing companies in this space are vendor lock-in, lack of transparency, and data sovereignty.
Vendor lock-in occurs when a business becomes too dependent on a particular cloud service provider, making it difficult or expensive to switch to another provider. Lack of transparency is a problem when companies are unsure of what security measures their cloud provider has in place, and how those measures are being implemented. Finally, data sovereignty is a concern when a business’s data is stored in a cloud service provider’s data center located in a different country, as it may be subject to different data privacy laws and regulations.
To mitigate these risks, businesses need to carefully evaluate cloud service providers before signing up, and should have contingency plans in place to switch to a different provider if necessary. It is also important to have clear contractual terms around data ownership, control, and access to avoid potential legal issues.
Emerging Trends in Cloud Security: Artificial Intelligence, Blockchain, and Zero Trust
As cloud technology continues to evolve, so too does cloud security. Three emerging trends in cloud security are artificial intelligence, blockchain, and zero trust.
Artificial intelligence is being used to enhance security by analyzing large amounts of data to identify patterns and anomalies that may indicate a security breach. It can also be used to automate threat detection and response, reducing the time it takes to identify and mitigate a security incident.
Blockchain technology is being explored as a way to increase the security of cloud storage and data sharing by providing a decentralized, immutable ledger that can be used to verify the integrity of data.
Zero trust is a security model that assumes that all users, devices, and applications are potentially compromised, and requires strict access controls and authentication for all users and devices.
As cloud security threats become increasingly sophisticated, it is important for businesses to stay on top of emerging trends and technologies to ensure the security of their data and systems. By incorporating artificial intelligence, blockchain, and zero trust into their security strategies, businesses can better protect themselves from threats and ensure the confidentiality, integrity, and availability of their data.
Conclusion: Ensuring Strong Cloud Security for Your Business
In conclusion, cloud security is a critical consideration for any business that stores or processes sensitive data in the cloud. As the use of cloud technology becomes increasingly prevalent, the risks and challenges associated with cloud security continue to evolve. To ensure strong cloud security for your business, it is important to:
- Carefully evaluate cloud service providers before signing up, and have contingency plans in place to switch to a different provider if necessary.
- Have clear contractual terms around data ownership, control, and access to avoid potential legal issues.
- Stay on top of emerging trends and technologies in cloud security, such as artificial intelligence, blockchain, and zero trust, to better protect your data and systems.
- Train employees on best practices for cloud security, including strong password management and avoiding phishing and other social engineering attacks.
By taking these steps, businesses can better protect themselves from security threats and ensure the confidentiality, integrity, and availability of their data in the cloud.