Cybersecurity and Internet Protection
Scanning is a method of keeping a security check on your devices. It shows any data breaches, harmful extensions, or any cookies that you might…
What is a digital footprint? And how to protect it from hackers
Introduction to Digital Footprints: What They Are and How They Work A digital footprint is the trail of data and information that a person leaves…
How to Determine If Your Laptop Camera Has Been Hacked?
You are seated in the comfort of your house or room and suddenly a thought occurs to you; someone is watching you through your computer!…
Omegle not working with VPN? Here’s how to FIX that!
Why Omegle May Not Work with VPNs Omegle is a popular online chat platform that allows users to chat with strangers from around the world.…
Understanding Phishing Scams: How to Protect Yourself Online In today's digital age, online security has become paramount. One of the most prevalent threats users face…
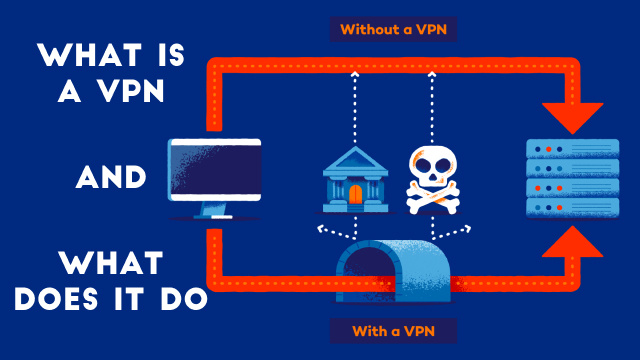
What is a vpn and what does it do
Defining VPN: A Comprehensive Guide A VPN, or Virtual Private Network, is a type of technology that provides users with a secure and private connection…
10 Ways to Tell If Someone Is Spying On Your Phone
Sudden decrease in battery life If you notice that your phone battery life is decreasing rapidly, it may be a sign that someone is spying…
The Pros and Cons of uTorrent uTorrent is a popular BitTorrent client that allows users to download and share large files over the internet. It…